We saw that real security requires cryptogaphy. But how can we combine both worlds?
- Biometrics
- Cryptography
- Combination
Biometrics
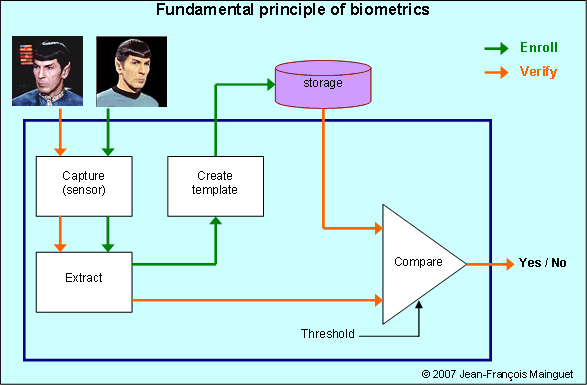
Fundamental principle of biometrics
As a reminder, here is the fundamental principle of biometrics:
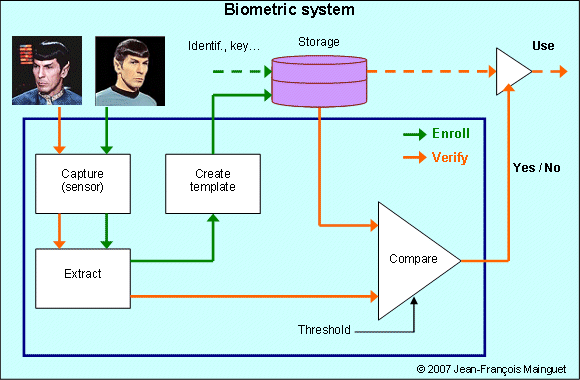
If we add the use, then we have a biometric system. Note that some additional data are required,
such as an identifier, a key or anything that will be useful to render the service.
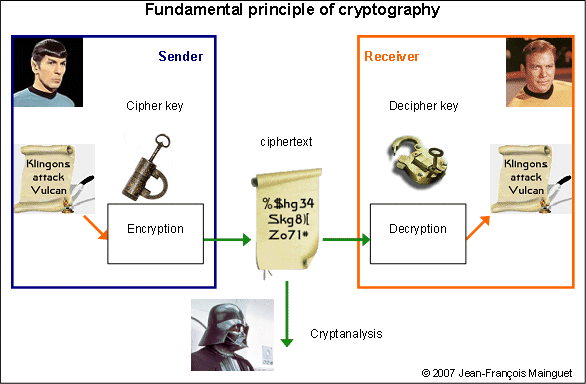
Cryptography
Fundamental principle of cryptography
Based on computation using a key.
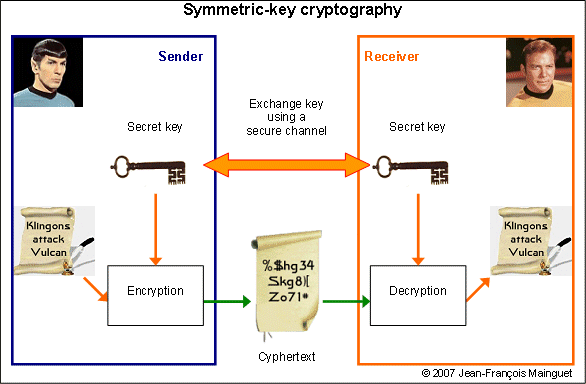
Symmetric key
A secret key is shared, and must cross at least once the public area, which is a problem.
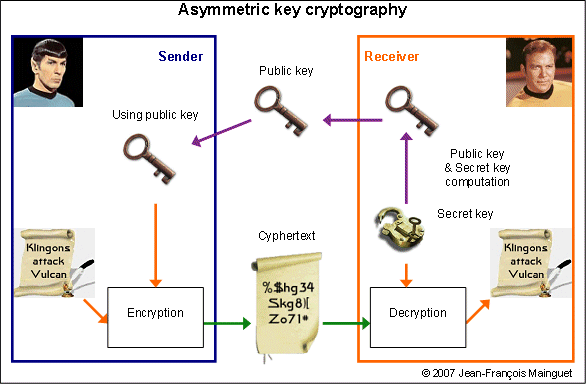
Asymmetric key
A public key is used to cypher data, a secret key to decypher.
There is no more the problem of transmitting a secret key, but the sender must be sure to use
the right public key (and not a impostor's public key).
Hashing
Fundamentally a one-way function (data loss).
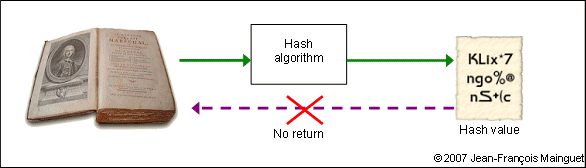
in the following, we don't care about some properties required for hash functions such as collision and fixed size. What is important is the fact that we have a one-way function, which will be useful when we want to cypher a biometric template: it is impossible to return to the original data.
Combining biometrics & cryptography
Protecting keys
This is one of the simplest use of biometrics: protecting the access to the secret key. But the biometric template is not protected: we should use also a secret key to protect the template. Houston, we got a problem! We cannot use biometrics to protect the key that will protect the biometric template, which give access to final secret key...
One usual application is the "password replacement": the fingerprint system is used to release the password to the application. The system is as secure as the password system -this is not better- BUT:
- this is more convenient
- and now you can use complicated long passwords that no one is able to find! (and don't forget to write it somewhere in a safe...)
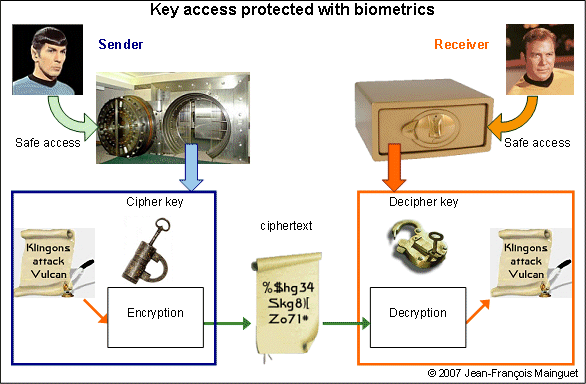
Where is the biometric template? Cyphered with the key that is inside the safe?
Of course, no,
as I would need the key to decipher the template to access the safe where is the key...
Cyphering template
We need to protect the template, so we use a secret key.
But where is stored this secret key that is used to protect the template?
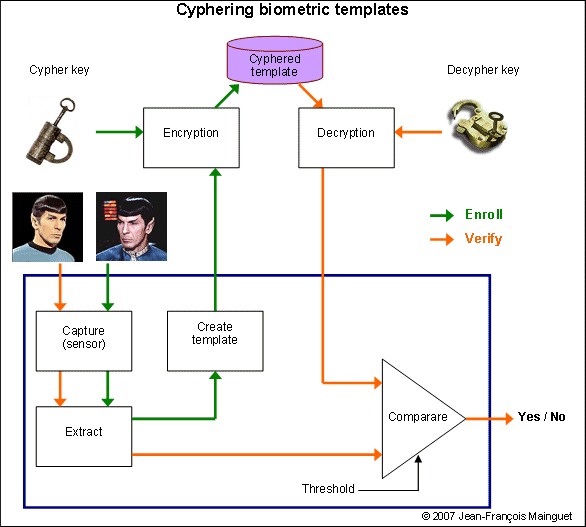
Hashing template / cancellable biometrics
Using a one-way function cypher the template, and no need to store a secret key.
This is sometimes called cancellable biometrics, because it is possible to revoke a template
and create a new one, not compatible with the previous one. But this definition is confusing
with what I call intricated or entangled biometrics.
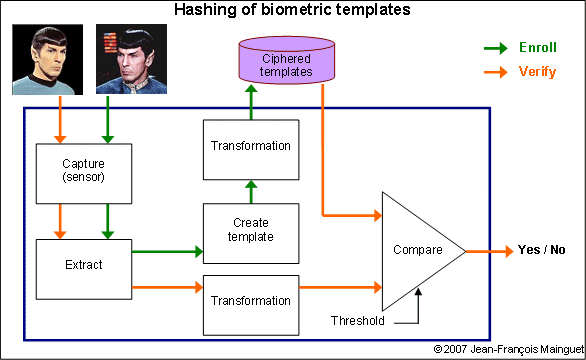
One difficult thing is to prove that you cannot return to the original biometric template
(is the transformation a real one-way function?).
Also, the comparison algorithm must be adapted, and proven not degrading the results.
Intricated/entangled biometrics
Here is a naive use of biometrics associated with a secret key.
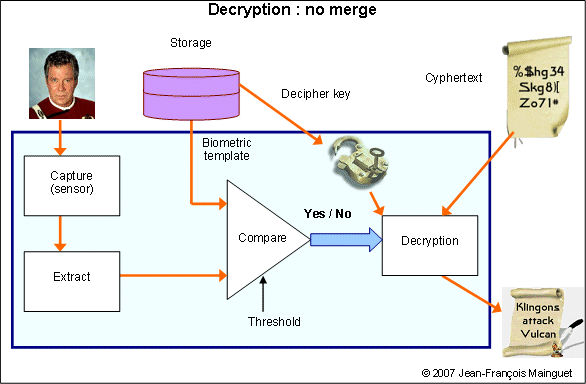
What is wrong in this scheme?
- The biometric template is readable, without protection!
- The secret key is readable, without protection! It appears in clear form!
- The entropy of the intermediate step is 1 bit, which is easy to break.
What we would like?
- A template from which it is impossible to get the original biometric information
- A template from which it is impossible to recover the secret key
- No intermediate step with a 1 bit entropy: during the process, the secret key is recovered in memory, used to decode the message and then deleted. If an impostor is trying to use the system, then a wrong key will be generated and the message will still be unreadable.
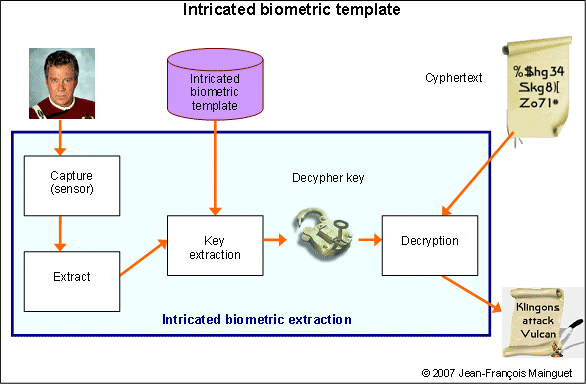
Is it possible to create such template? The answer is yes. But explaining that is pretty hard, you will need to read some of the document cited below. And unfortunately, there is no proven system working like that today. And so yes, you may be afraid of how cryptography is used in real systems...
Exemple use:
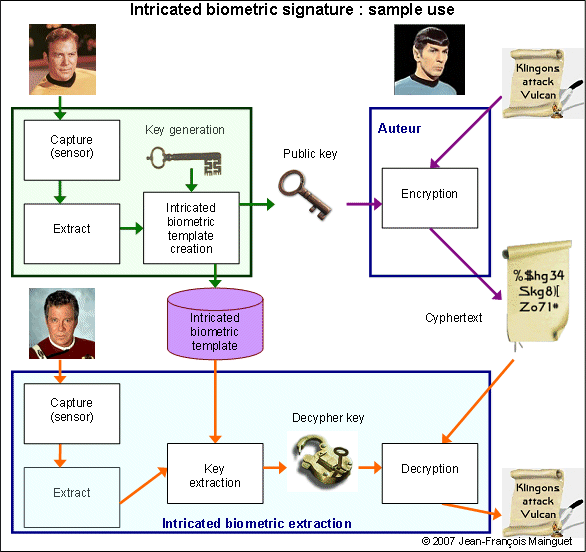
Everything is public at the end: when generating the secret key, it is destroyed at enroll, and appears in memory only a short while for decryption. Also, it is not possible to use the template for another use, crossing databases is just impossible.
Some links for more information, as a start
- "Biometric encryption: A positive-sum technology that achieves strong authentication, security and privacy". Ann Cavoukian and Alex Stoianov. White paper, Information and privacy commissioner of Ontario, March 2007.
- "Biometric Encryption", C. Soutar, D. Roberge, A. Stoianov, R. Gilroy, and B.V.K. Vijaya Kumar. chapter 22. McGraw-Hill, 1999.
- "Enhancing security and privacy in biometrics-based authentication systems". N. K. Ratha, J. H. Connell, and R. M. Bolle. IBM Systems Journal, 40(3):614-634, 2001.
- "On the relation of error correction and cryptography to an off-line biometric based identification scheme". G. I. Davida, Y. Frankel, B. J. Matt, and R. Peralta. In Proc. Workshop on Coding and Cryptography, pages 129-138,1999.
- "New shielding functions to enhance privacy and prevent misuse of biometric templates". J.P. Linnartz and P. Tuyls. In Proc. 4th Int. Conf. Audio and Video based Biometric Person Authentication, pages 393-402, 2003.
- "An impoved biohashing for human authentication". Alessandra Lumini and Loris Nanni. Pattern Recognition, 40:1057-4065, 2007
- "Revocable Fingerprint Biotokens: Accuracy and Security Analysis," Boult, T. E.; Scheirer, W. J.; Woodworth, R., /IEEE Conference on Computer Vision and Pattern Recognition, 2007. CVPR '07. / , vol., no., pp.1-8, 17-22 June 2007
- "Fuzzy extractors: How to generate strong keys from biometrics and other noisy data". Y. Dodis, L. Reyzin, and A. Smith. In Proceedings of the Eurocrypt 2004, pages 523-540, 2004.
- "A biometric identity based signature scheme". A. Burnett, F. Byrne, T. Dowling, and A. Dury. In Proceedings of the Applied Cryptography and Network Security Conference, 2005.
- "Biometric cryptography: Key generation using feature and parametric aggregation". Christopher Ralph Costanzo. Online techreport, School of Engineering and Applied Sciences, Department of Computer Science, The George Washington University, October 2004.
- "Crypto key generation using contour graph algorithm". M.S. Al-Tarawneh, L.C. Khor, W.L. Woo, and S.S. Dlay. In Proceedings of the 24th IASTED International Multi-Conference Signal Processing, Pattern Recognition and Applications, February 2006.
- "A fuzzy vault scheme". A. Juels and M. Sudan. In A. Lapidoth and E. Teletar, editors, Proc. IEEE Int. Symp. Information Theory, page 408. IEEE Press, 2002
- "Hiding secret points amidst Chaff". Ee-Chien Chang and Qiming Li. In Proceedings of the Eurocrypt 2006, 2006
- "Cryptographic key generation from biometric data using lattice mapping". Gang Zheng, Wanqing Li, and Ce Zhan. In ICPR '06: Proceedings of the 18th International Conference on Pattern Recognition, pages 513-516, Washington, DC, USA, 2006. IEEE Computer Society
- "Fuzzy fingerprint vault". Umut Uludag and Anil K. Jain. In Proc. Workshop: Biometrics: Challenges Arising from Theory to Practice, pages 13-16, August 2004.
- "Securing fingerprint template: Fuzzy vault with helper data". U. Uludag and A. Jain. In Proc. of the 2006 Conference on Computer Vision and Pattern Recognition Workshop, pages 163-170, June 2006
- (2010) ISO 24745 - Biometric Template Protection / Christoph Busch
- Biometrics / Dr Andrzej Drygajlo (EPFL) [I would appreciate a citation...]
 |
 |